Security is key to keeping cybercriminals at bay
To catch a sophisticated cybercriminal in today’s age, IT departments must look deeper into their web traffic and examine many sources of information about web visitors and sessions to determine what behavior is typical and what is not. Existing solutions for detecting and analyzing online criminal behavior usually identify either pre-authentification threats , or post authentification threats (fraud products) but unfortunately not both.
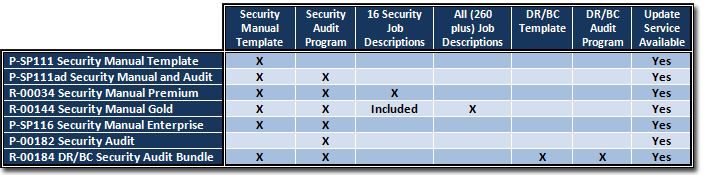
- Security Manual Template (Policies and Procedures) (ISO Compliant)
- Security Manual Template and Audit Program
- Security Manual Template and Disaster Recovery Business Continuity Template Bundle
- Security Manual Template, Disaster Recovery Business Continuity Template, and Safety Program Bundle
- Security Manual Template and Disaster Recovery Business Continuity Template Audit Bundle
- Payment Card Industry (PCI) Data Security Audit Program
- Payment Card Industry (PCI) Data Security Standard PCI-DSS Compliance Kit
- Security Audit Program
- Patriot Act Security Bundle
- Compliance with HIPAA Standards
- Compliance with FIPS 199
- Threat and Vulnerability Assessment
- Threat Risk Assessment Extended Service